SHORT NEWS
Behavior-based authentication as an alternative to a plethora of passwords
Whether when typing, moving, or walking, scientists are investigating how devices recognize users by their behavior.

Passwords have a number of drawbacks: they are often not sufficiently protected by online service providers or by the users themselves, they can be stolen, and ideally they are so complex that it is difficult to remember a different password for each service.
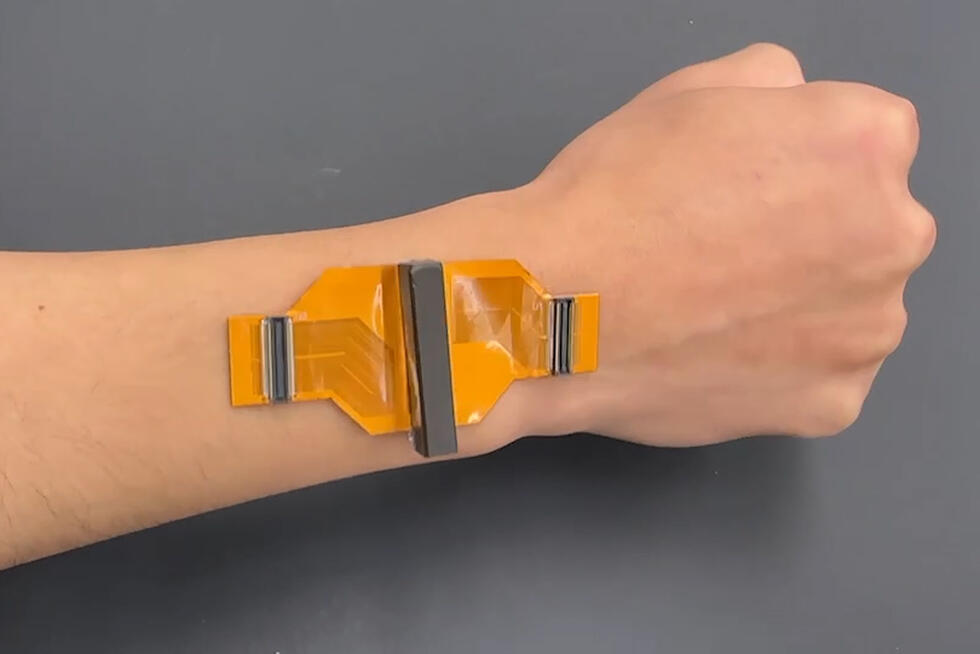
A secure and promising alternative is behavior-based authentication, which scientists at the Hasso Plattner Institute (HPI) in Potsdam, Germany, are researching. This can be done using a variety of behavioral patterns, such as typing on a keyboard, the movement a user makes to take their smartphone out of their pocket, or the individual gait. In this context, external influences on the gait, such as different clothing or associated activities such as telephoning, are also being investigated.
A special research approach uses sensors in mobile devices such as smartphones or wearables for the secure verification of identities. From the individual behavior they calculate a percentage value, the trust level. This trust level is sent to the corresponding online service instead of a password, which itself determines how high this value must be for the use of its service. If a smartphone is stolen, the trust level drops and all access is locked.
“This approach has many advantages: It is secure, very user-friendly, and is even cost-effective, since most people own a smartphone and no additional hardware is required,” says Professor Christoph Meinel, the HPI Director and Head of Internet Technologies and Systems. "Another big advantage is that the users’ biometric data remains on their devices and is not passed on to external service providers. Only the calculated trust level is transmitted. But unlike passwords, this is not of any interest to criminals. The first applications for behavior-based authentication are already being tested in practice by the HPI startup neXenio. For example, thousands of employees automatically unlock the doors of a New York skyscraper once the required trust level has been transmitted from the end device to the door. At another large company, the access and use of selected machines is controlled via the developed app.